Now available for WordPress
Check it out


Credential stuffing, stolen passwords, and automated fraud attacks put your users — and your platform — at risk. Trusted Accounts detects suspicious logins, blocks account takeovers, and keeps real users secure without adding friction.


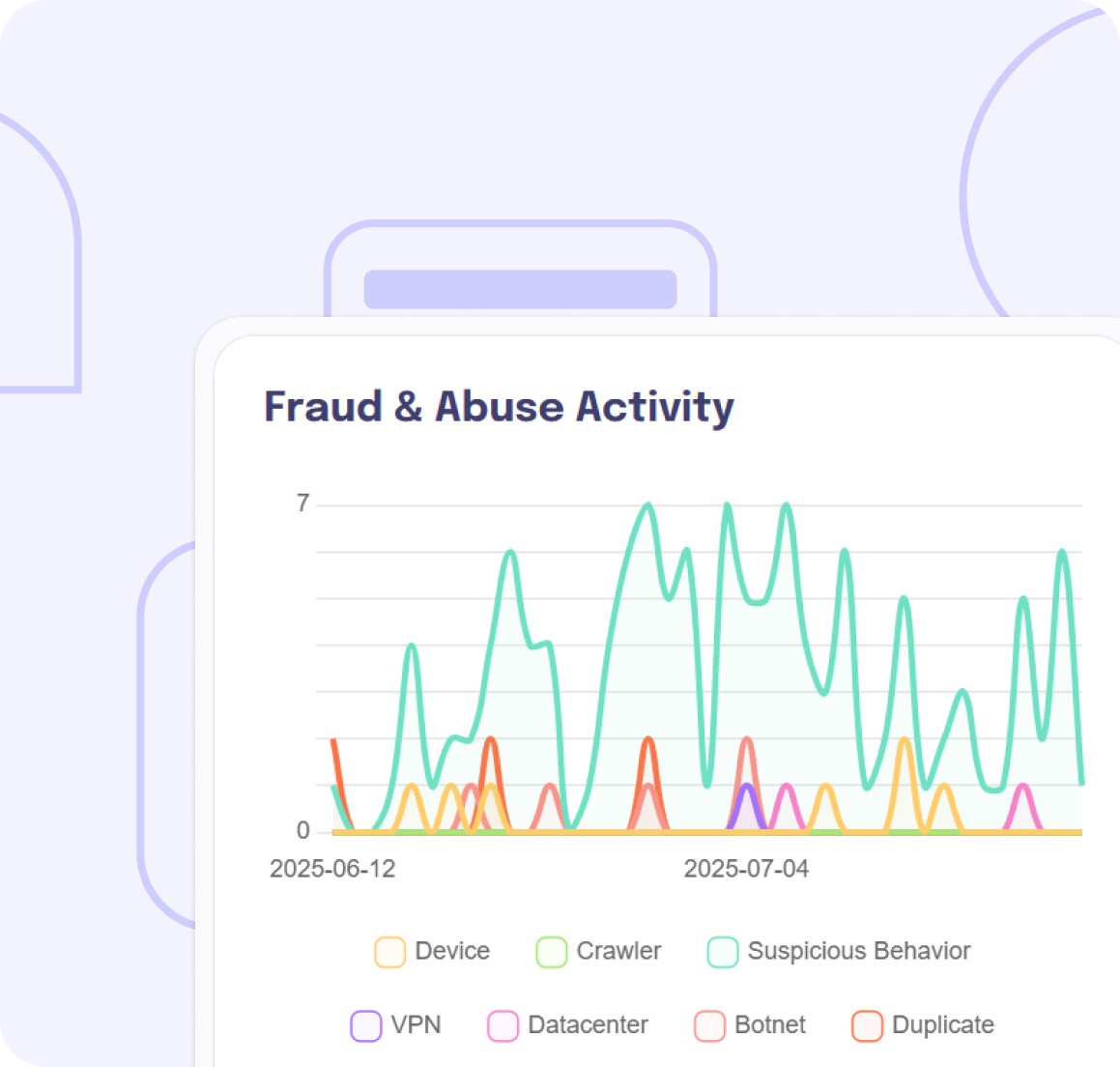


Catch Risky Logins
Detect suspicious logins and credential stuffing attacks

Block Takeovers Fast
Block automated takeover attempts before they succeed

Monitor Fraud Signals
Monitor user activity for fraud indicators in real time

Protect Users Seamlessly
Keep real users protected without extra steps

News & Publishers
Let your community grow.
Community Platforms
Stop fake accounts, spam, and poll manipulation. Keep your community real and trusted.
E‑Commerce
Prevent promo abuse, fake reviews, and account fraud. Protect customers and your revenue.
SaaS Platforms
End trial abuse, bot signups, and fake accounts. Keep analytics and resources clean.
Marketing
Cut click fraud, fake leads, and bot traffic. Optimize campaigns with real data.

Whether you run a news site, e‑commerce store, or community platform, the threats are the same. Here’s how we protect you from the most damaging ones.






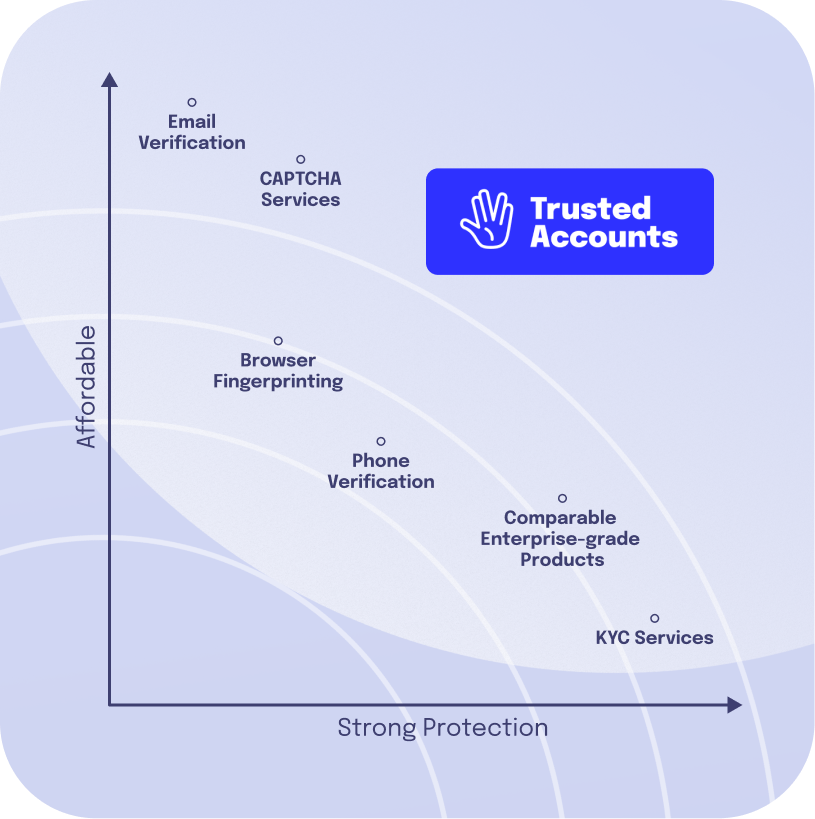




„In Trusted Accounts, we see the potential to increase our verification rate and thus be able to moderate fake accounts, trolls, hate and disinformation more efficiently.”

Head of Product, DER STANDARD

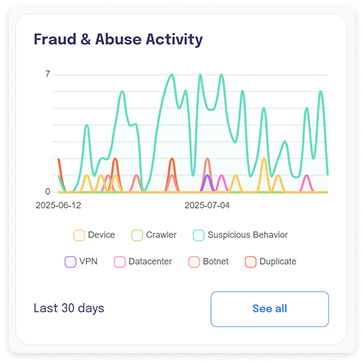

Fraud & Abuse Protect
Spot fake accounts, ad fraud, survey manipulation, disinformation, and more.

Account Protection
Silent checks for authentic users, extra checks only for suspicious users.


Stop Bots and Abusive Users: Protect Your WordPress Site with Trusted Accounts

Future-Proofing Content Moderation: Use Cases for 2024

Bot Protection - Top 7 Tools for 2024

We analyze login behavior, device fingerprints, and usage patterns to flag suspicious logins and block automated credential stuffing attempts.

No — most checks are invisible. Only risky logins trigger additional verification.

Yes — our system detects automation as well as abnormal user behavior that signals fraud.

Yes — Trusted Accounts connects with major authentication flows and custom systems via API.

Most platforms detect takeover attempts and see reduced fraud within 24–48 hours of setup.

